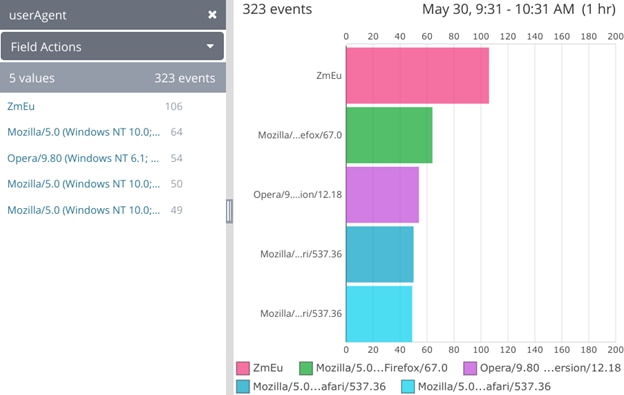
Radware's Quarterly DDoS and Application Attack Report provides an overview of attack activity witnessed during the third quar

KubAnomaly: Anomaly detection for the Docker orchestration platform with neural network approaches - Tien - 2019 - Engineering Reports - Wiley Online Library
Radware's Quarterly DDoS and Application Attack Report provides an overview of attack activity witnessed during the third quar

KubAnomaly: Anomaly detection for the Docker orchestration platform with neural network approaches - Tien - 2019 - Engineering Reports - Wiley Online Library